Expiring email? no, not really
The sales pitch
Here's a couple of choice quotes from BigString's about page and FAQ:
- "BigString’s emails look and feel like any other emails that you get"
- "If the sender chooses the non-print/non-save feature, then the email, while looking like every other email, will print nothing when the receiver clicks print on the computer and show nothing if the receiver tries to save the text or image.
How it works
BigString (or maybe we'll just call them BS for short) doesn't just send the words you type, that would leave the recipient with total control (as is the case for regular email). Instead, they make a picture of your words, store that picture on their web server and send an HTML email that has an embedded link to that picture.
Myth #1: BS messages look & feel like other email messages.
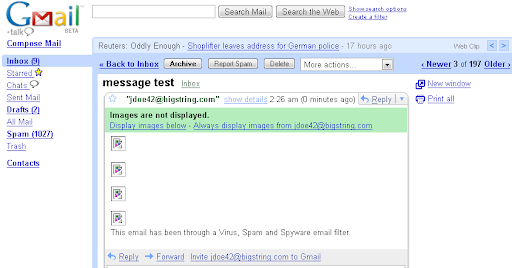
As far as BS claim #1, it doesn't look like other email I receive. Even after clicking to show images, it doesn't feel like other email I receive... the text doesn't wrap to my window width (obviously, because it's an image, it can't).
Myth #2: Can't save, print, copy or forward email
Since they're hosting the image on their server, they do have some control. Primarily, they can delete the image from their server so that it won't show up anymore. Does that make it hard to save, print, copy or forward? Well, if you use the buttons in your email client, the way you would for normal email, you'll find that messages do disappear. But due to the initial display as shown in the screenshot above, you've already been tipped off that this isn't a normal message.
There are two one-click methods that anyone receiving such a message can do to preserve the content:
- Hit the PrintScreen key - It's been a built-in feature of Windows since Win95... just a single press and the entire contents of your screen are on the clipboard. You can then easily paste that into something like Paint (comes with Windows), a word processor, and even some email clients (e.g. Thunderbird). Tools like ScreenPrint32 and Directory Opus make the task even easier.
- When viewing the message in a web browser (using Firefox or IE to check your Gmail or Yahoo mail), you can right-click on the message content and choose Set As Desktop Background.
Looks to me like this message hasn't really expired. Not only that, but I've managed to copy it and post it for the world to see... a bit more wide-spread than forwarding it. You can even print it.
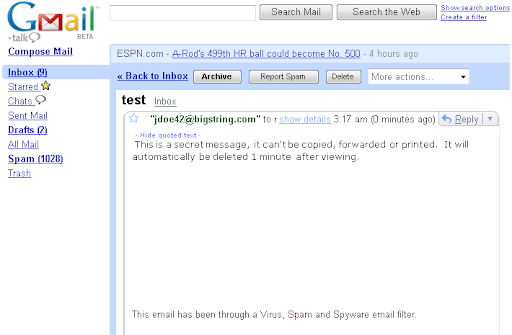
Other problems with BS:
- I download all my mail before getting on a plane and compose replies that I'll send when I get off. Having messages from someone that show up as broken image icons means they get thrown in the trash... guess that person didn't really want me to see the message.
- Email messages that are comprised solely of images are typically spam... meaning that spam filters are likely to catch mail from BS.
- The only text in the messages sent from BS is "This email has been through a Virus, Spam and Spyware email filter." That's really reassuring! I bet no virus author would ever think of including that bit of text in their email. I think I need to re-iterate one of my previous points: BS is doing its customers a dis-service... it's providing them a false sense of security.
Is there a workable solution?
Well, in general, if you can see it on your screen, you can save it. Can a program try to stop you? Sure, but it's a losing battle:
Stopping the right-click menu:
It's possible for JavaScript code to block the right-click menu in web browsers. But browsers have the final say in what they allow. For example, in Firefox, got to Tools->Options->Content and next to "Enable JavaScript", click Advanced... Uncheck the box that allows scripts to "Disable or replace context menus".
Stopping the PrintScreen key:
A message could be delivered as an executable that prevents use of the PrintScreen key. Forgetting for a moment that you've just made the message unreadable to all but one operating system and broken one of the cardinal rules of email: don't attach executables, many mail gateways won't even bother running a virus scan, they'll just delete the message. How would a recipient work around your clever program that breaks the PrintScreen key? The word camera comes to mind here...
My proposal
How do you make messages are easy for a person to read, but hard to save/print/forward/copy? Well, you have to make some sacrifices. In particular, you have to loosen up on the "easy for a person to read" part... how about starting with "possible for a person to read and no more inconvenient than necessary".
If I wanted to prevent people from using the PrintScreen key, then I'd have to make sure that it wasn't just a way of disabling the key on the keyboard... it has to be something that a camera can't capture either. The best way to do that is to make it be interactive.
The simplest interface I can think of is this:
- You open your inbox and have a message from me. It reads:
- You click the link and it's a web page that uses Flash.
- The message is black text on a black background. Your mouse works like a flashlight that will only illuminate the text close to the pointer.
It's far from perfect. If someone sent me a long message that way I hope they wouldn't expect me to read the whole thing. Meanwhile, instead of a camera, it would take a camcorder. Instead of PrintScreen, it would take screen recording software. It is harder for the user to capture, and you can easily dress it up with a cloak & dagger theme to add to the experience.
Bottom line: self-destructing email isn't. If you believe in it, your worse case may be similar to Michael Crooker, who believed Compaq when they said even they couldn't decrypt a secure hard drive.